Consensus mechanisms are the unsung heroes of the blockchain world. They work behind the scenes to enable the magical concept of crypto currency and decentralized applications we all know and love.
But how do they turn a distributed network of potentially untrustworthy nodes into an unhackable blockchain? Well, it’s nothing short of alchemy. Blockchain consensus protocols brew together cryptography, game theory, and community collaboration to arrive at a conclusion.
In this blog, we'll unveil the inner workings of the consensus algorithms powering blockchain networks – the black magic of proof of work and proof of stake protocols, and the likes of them.
By peering inside the blockchain beast and demystifying consensus protocols, you'll also gain a deeper appreciation for these unsung algorithms and the distributed ledger technology at large. Then, let's lift the curtain and shed some light on what is consensus in blockchain!
This Article Contains:
What is the consensus algorithm in blockchain?
Stop thinking in technical terms for a while. Just think of a consensus algorithm like a big potluck dinner with 100 guests.
Everyone brings a dish to share, but they don't know or fully trust each other. Maybe it’s a vegan potluck and the community would want to blacklist anyone who brings non-vegetarian items. Who knows? But, how do they keep track of who brought what without a central planner overseeing everything?

That’s where the “consensus algorithm” works its magic! It allows the untrusting potluck participants to agree on what dishes were brought and who brought them.
So, this blockchain potluck community decides that a few people will voluntarily verify the food items. They will write down the name of the person, the dish that they bring, and the time at which they bring it.
It comes up with a set of rules, i.e.,
All potluck participants must announce their names while placing their food items on the table.
All volunteer verifiers must record the name, dish, and time for each item brought in the master list.
Every dish must be in the right order as per its timestamp.
The verifiers must announce the order of the list after every 5 dishes.
The records must be compared, and any conflicts resolved through a majority vote.
This is essentially how a blockchain consensus algorithm works – by coordinating agreement on the state of the network among distributed nodes. The nodes are like potluck guests and the data is the food they bring. The rules allow them to arrive at a consensus despite not fully trusting each other. Verifiers, also known as miners, are the people who dedicate their computing power to mining.
Remember, given the immutable nature of the blockchain, no previous entry on the list can be erased or overwritten. The record can only be appended with new entries that are verified.
Also Read: What is Blockchain Technology?
For example, during our potluck, suppose Anne brought a pasta salad that got incorrectly recorded as a potato salad, the master list would need to be updated. At least 51% of the potluck validators would have to reach a consensus that Anne actually brought pasta salad.
Once agreed, the master list is updated accordingly, with the original erroneous entry remaining intact. This demonstrates how consensus enables decentralized ledgers to be resistant to manipulation.
The validated record becomes the single source of truth. Any questionable guest who tries to falsely add a dish will get caught during the verification process.
Note: There are several ways in which malicious operators can still affect a blockchain, which we will discuss later.
Technically Speaking: What is a Consensus Mechanism?
Like the potluck we just discussed, a blockchain consensus algorithm allows the nodes in a decentralized network to agree on the ledger's state and verify new transactions securely, without needing a central authority.
Consensus algorithms achieve this through a set of defined rules and procedures that all participating nodes must follow. The protocols create alignment without complete trust between nodes. Hence, they are also referred to as trustless. A key role is played by validator nodes, who are responsible for bundling transactions into blocks and certifying their validity before adding them to the blockchain.

Validators apply various cryptographic checks and enforce protocol rules to filter out invalid transactions or blocks. This is crucial for maintaining the overall integrity of the ledger.
Different consensus models use varying approaches to facilitate node agreements while disincentivizing cheating. For example, proof-of-work relies on mining computational power whilea proof-of-stake leverages validator deposits.
Once a new block is validated by enough nodes to meet the predetermined threshold (usually a majority), the block is set in stone from there. The accepted block is broadcasted to all nodes to append to their blockchain copies.
This decentralized process continues sequentially, with each new block cryptographically chained to prior blocks. Consensus protocols enable blockchains to scale while retaining key attributes of immutability, transparency, and security.
Some salient features of a consensus mechanism
Nodes on the network follow a pre-defined consensus protocol that specifies the rules and procedures for validating transactions.
Specific nodes take on the role of validators, who are responsible for bundling transactions into block candidates and verifying their validity (like the designated validators in our potluck example).
Validators apply cryptographic checks, enforce protocol rules, and leverage mechanisms like economic stakes to achieve consensus on new blocks.
The agreement is typically reached once a majority threshold of nodes confirms a block is valid based on the consensus algorithm (like 51% of potluck guests agreeing on the dish brought by Anne).
Protocols must deter malicious actors from manipulating consensus.
Finalized blocks are broadcast to all nodes who append the accepted block to their copy of the ledger.
Consensus protocols enable key blockchain properties like immutability, security, and decentralization without a central coordinating authority (no central potluck overseer needed).
Proof of Work vs. Proof of Stake: What’s the difference?
There are several consensus protocols including Proof of Work, Proof of Stake, Proof of Authority, and Practical Byzantine Fault Tolerance to mention a few.
However, before delving into all of them, let’s differentiate between the two most heavily discussed consensus mechanisms to date, i.e., Proof of Work (PoW) and Proof of Stake (PoS).
PoW is the foundational consensus mechanism mentioned in Satoshi Nakamoto’s original Bitcoin paper. Like Bitcoin, Ethereum also originally utilized a proof-of-work (PoW) consensus model called Ethash. Being the foundational stone for Bitcoin and blockchain technology at large, Proof of Work holds a special place in all blockchain enthusiasts’ hearts.

In Ethereum's PoW system, miners competed to solve a cryptographic puzzle to validate new blocks.
Once mined, new Ethereum blocks would then pass several verification steps checked by all nodes, like:
Validating the block data structure
Checking the block header hash
Confirming the timestamp is sequential
Ensuring block size is below the limit
Verifying the first transaction in the block
Proof of Work served Ethereum well in its early years. However, it came with drawbacks like high energy consumption and difficulty scaling. Also, the likelihood of mining rewards consolidating among a few large miners raises decentralization concerns.
This led Ethereum to transition to a Proof of Stake (PoS) consensus model in 2022. Proof of Stake relies on validators staking ETH instead of miners competing to solve puzzles.
In PoS, validators take turns proposing and validating new blocks. To become a validator, users must stake 32 ETH as collateral. This stake incentivizes validators to act honestly, or else they risk losing their deposit.
The PoS validator selected to propose the next block is known as the leader. They bundle pending transactions into a block and broadcast it to the network.
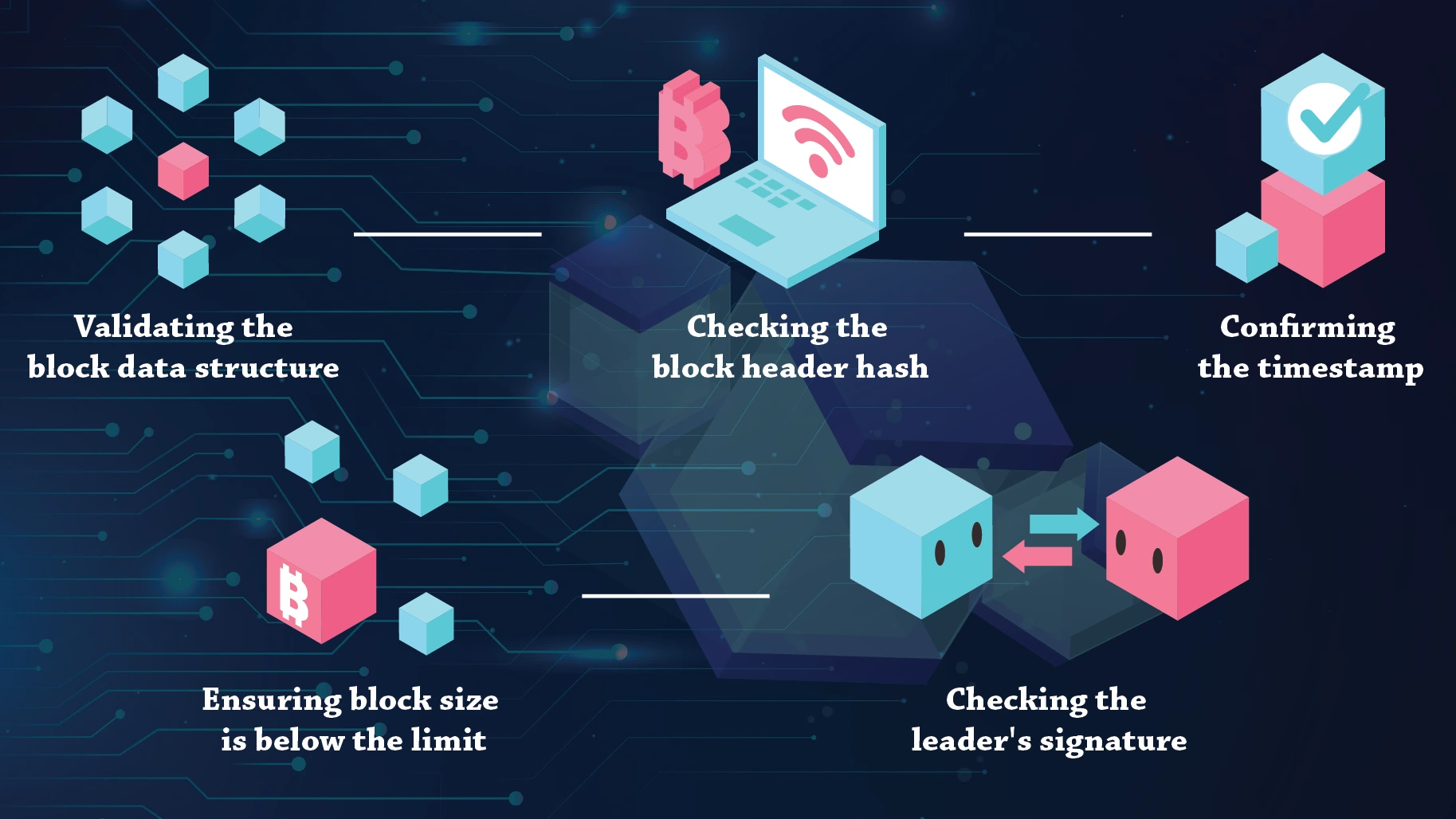
The block then goes through several verification checks by other validators, similar to PoW:
Validating the block data structure
Checking the block header hash
Confirming the timestamp
Ensuring block size is below the limit
Checking the leader's signature
Once two-thirds of validators attest the block is valid, it is finalized and added to the blockchain.
Compared to PoW, PoS offers improved security, scalability, and energy efficiency. Staking also allows regular users to participate in block production by becoming validators.
While PoW and PoS take different approaches, they both enable public blockchains to achieve consensus in a trustless decentralized environment. Consensus protocols are key to blockchain's tamperproof and transparent record of transactions.
Different Types of Consensus Mechanisms
Proof of Work (PoW)
Introduced by Bitcoin in 2009, PoW is the first consensus mechanism for blockchains. It marked a breakthrough in achieving decentralized consensus without a central authority.
Miners compete to find a nonce value that, when combined with the block's data, produces a hash below a predefined target. The first miner to discover such a hash is rewarded with newly minted coins and transaction fees. Achieving the target hash requires repeated cryptographic hashing, which is resource intensive.
Advantages:
High security: Performing malicious attacks on a PoW network would require enormous computational resources, making them prohibitively expensive. This deters malicious actors.
Decentralization: Anyone with sufficient hardware and electricity can participate in mining and earn coin rewards. This leads to a decentralized distribution of coins.
Immutable transaction history: Revising past transactions requires redoing the proof of work, making the transaction history tamper-resistant.
Disadvantages:
High energy consumption: The computational intensity of cryptographic hashing requires massive amounts of electricity, raising environmental concerns.
Hardware arms race: Increased mining difficulty leads to an arms race in specialized mining hardware, which tends to centralize mining power and rewards.
Scalability issues: PoW networks have limited transaction throughput due to the time required for block confirmations.
Proof of Stake (PoS)
In Proof of Stake, validators are chosen to create new blocks based on the amount of cryptocurrency they "stake" or "lock up" as collateral. Their probability of being selected is proportional to their staked amount. Staked tokens are forfeited if the validator acts maliciously.
PoS was introduced to address PoW's energy consumption issues and improve scalability. It eliminates computationally intensive mining.
Advantages:
Energy efficiency: PoS eliminates mining, drastically reducing energy usage compared to PoW.
Lower barrier to entry: Participants can become validators by staking coins rather than investing in powerful hardware. This is more accessible.
Scalability: PoS enables mechanisms like sharding to greatly improve transaction throughput.
Disadvantages:
"Nothing at stake" problem: Validators can vote on multiple forks without repercussion, leading to consensus instability.
Centralization risks: Wealthy participants have greater influence over the network as validators. This raises centralization concerns.
Delegated Proof of Stake (DPoS)
DPoS aims to increase efficiency and scalability compared to PoW and PoS.
In this consensus mechanism, token holders vote for delegates who take turns validating transactions and creating blocks in rounds. Voting power is proportional to token holdings. Some implementations of DPoS include TRON and EOS. While TRON uses Super Representatives and conducts elections every 6 hours, EOS has all of its delegates as block producers and elections take place every few minutes.
Advantages:
High transaction throughput: With fewer validators, blocks can be produced rapidly, increasing throughput.
Voting rights for stakeholders: Token holders can vote out malicious delegates, giving them oversight over the network.
Efficiency: Consensus is reached with low computational overhead.
Disadvantages:
Voting apathy and collusion: Voters may become apathetic over time, allowing delegates to collude or act negligently.
Centralization risks:Voters tend to favor prominent delegates, leading to the centralization of validation power..
Regulatory uncertainty: The voting mechanisms resemble securities, raising potential regulatory issues.
Proof of Authority (PoA)
In Proof of Authority, block validators are pre-approved entities who take turns creating blocks. They are typically companies or institutions that agree to uphold network rules. Some popular implementations of PoA include VeChain, Bitgert, and Xodex.
PoA improves consensus speed and efficiency for permissioned blockchains by relying on identified validators.
Advantages:
Fast consensus: Removes the need for block mining, enabling faster block times.
Use case optimized: Suitable for private networks where participants are known and trusted.
Lower barriers: Does not require expensive mining hardware to participate.
Disadvantages:
Centralization: Reliance on approved validators introduces centralization based on their identities.
Collusion risk: Validators may collude to alter network rules if oversight is insufficient..
Lower barriers: Unsuitable for public networks requiring open participation and censorship resistance.
Proof of Space (PoSpace)
In this consensus mechanism, miners commit disk space rather than computation to participate. The more unused space committed, the higher chance of being selected to create blocks.
PoSpace was popularized by Signum (formerly Burstcoin) and substitutes disk space for the compute-intensive mining required by PoW.
Note: Signum has since moved to Proof of Capacity, which is similar but slightly different consensus mechanism.
Advantages:
Reduced energy use: Eliminates computational mining in favor of unused disk space.
More accessible mining: Allows broader participation with spare disk capacity rather than specialized ASICs.
Storage synergy: Disk space commitment enables additional use cases like distributed file storage.
Disadvantages:
Hardware centralization:Data centers with major storage capacity could dominate participation.
Space accumulation:: Participants may hoard storage to increase their mining odds.
Proof of Capacity (PoC)
Similar to PoSpace, in this consensus mechanism, miners generate and store large datasets to prove their storage capacity and win block rewards. The more capacity committed, the higher the chance to create blocks. PoC focuses on provable spare storage capacity rather than intensive computations.
PoC requires miners to allocate storage with data plotted on it (using functions like Shabal hash), while Proof of Space only requires allocating unused storage space. In PoSpace, during mining, random sections of the allocated space are challenged to provide proofs, and miners just have to allocate unused storage space, no initial plotting is required. However, in PoC, data plotted serves as "proof" that storage and computation were committed to mining.
Advantages:
Energy efficiency: Like Proof of Space, it eliminates PoW computations, reducing energy consumption.
Accessibility: Allows participation using consumer-grade hardware such as hard drives.
Quick syncing: Committed datasets enable new nodes to rapidly sync to the network.
Disadvantages:
Initial setup costs:Generating and storing the datasets used in proofs requires substantial disk space.
Centralization risks: Data centers could potentially dominate participation by committing massive storage.
Possible malware injection: The mechanism opens the door for possible malware injections affecting the mining operations.
Criticized for disk deterioration: Some blockchains, including Chia, are criticized for possible hard disk damage under unmonitored and unmaintained circumstances.
Proof of Burn (PoB)
To demonstrate commitment, PoB miners send tokens to addresses from which they can never be redeemed, effectively destroying them. Miners gain the right to validate in proportion to the number of coins burned. Some examples include Counterparty and Slimcoin (hybrid).
PoB aligns incentives by requiring validators to demonstrate commitment through a provable destruction of tokens.
Advantages:
Aligns incentives: Coin burns demonstrate a miner's commitment to the network.
Deflationary: Permanently removing coins increases scarcity, potentially raising the value of remaining coins.
Fair distribution: The act of burning coins enables broader participation in validation based on willingness to destroy coins.
Disadvantages:
Token loss: Validators permanently lose coins they burn, which could reduce incentives to participate over time.
Deflation issues: The decreasing circulation could increase hoarding behaviors detrimental to commerce.
Sybil resistance risks: Burning small amounts of coins may not sufficiently deter Sybil attacks.
Proof of Elapsed Time (PoET)
In this consensus mechanism, miners randomly wait for a period, and the first to complete the wait interval wins the right to propose the next block. The waiting time is proven in a trusted execution environment.
PoET, used in Hyperledger Sawtooth, aims to reduce energy usage in block creation by replacing computations with a random wait time.
Advantages:
Energy efficiency: Removes the computational work required by PoW.
Permissionless mining: All miners have an equal probability of being selected to create blocks.
Use case optimization:The reliance on trusted hardware makes it suitable for permissioned networks.
Disadvantages:
Trusted hardware dependence: Requires Intel SGX or similar trusted execution environments.
Limited scalability: Performance remains bound by the security limits of the trusted hardware.
Centralization risks: Could potentially concentrate in data centers with specialized trusted hardware.
Proof of Identity (PoID)
PoID integrates legal or social identity with blockchain consensus. On this consensus algorithm, validators submit verified real-world identities and undergo ongoing identity verification to participate in consensus.
This promising consensus mechanism is solving challenges like intensive documentation for various use cases. For instance, World Economic Forum’s Known Traveller Digital Identity aims to decrease the documentation of global travelers without compromising on security.

Advantages:
Sybil resistance:Discourages fake identities by requiring verified identities.
Accountability: Validator’s actions can be attributed to real-world identities.
Compliance: Adherence to PoI enhances compliance in regulated sectors.
Disadvantages:
Centralization:Consolidation around approved identity providers could lead to centralization.
Privacy risks: Linking identities could reveal personal data and activity patterns.
Proof of Reputation (PoR)
In this consensus mechanism, a validator's reputation determines its chances of being selected to propose blocks. Reputation scores evolve over time based on historical behavior.
PoR aims to improve Sybil resistance and encourage good behavior by factoring reputation into consensus, as in the case of GoChain.
Advantages:
Sybil attack resistance: Requiring established reputation makes faking identities more difficult.
Incentivizes good actors: Validators are motivated to build and maintain positive reputations over time.
Flexible source of reputation: Can leverage various online/offline reputation systems.
Disadvantages:
Difficult to design: Quantifying and calculating effective reputation scores is challenging to get right.
Subjective metrics: Reputation scoring relies on subjective trust metrics.
New entrant barrier: Onboarding new validators is difficult due to the initial low reputation.
Proof of Weight (PoWeight)
Similar to PoS, PoWeight validators are selected based on their "weight" – a metric calculated from factors like the age of coins, transaction volume, and token holdings. Nodes with higher weight have greater chances of proposing blocks. Algorand is built using this approach and calls its consensus mechanism Pure Proof of Stake(PPoS.)
This consensus mechanism introduces alternative selection criteria beyond just staked tokens, aiming for fairer and more decentralized participation.
Advantages:
Encourages long-term commitments: Prioritizing older coins motivates holding over short-term speculation.
Mitigates centralization risks: Basing weight on multiple factors prevents the concentration of power based solely on wealth.
Flexible source of reputation: The weighting metrics can be tailored for different use cases.
Disadvantages:
Difficulty in picking metrics: Designing an effective weighting formula is challenging. Poorly chosen metrics can worsen centralization.
Subjective metrics: Computing weight factors like transaction volume requires accumulating extensive historical data.
Byzantine Fault Tolerance (BFT)
BFT protocols allow nodes in a distributed system to reach consensus even if some of the nodes are malfunctioning or malicious. This is achieved through mechanisms like voting rounds, cryptographic techniques, and assumptions on the maximum number of faulty nodes.
BFT provides a solution to the Byzantine General’s Problem in distributed computing, allowing consensus despite untrusted participants.
Advantages:
Resilience to attack vectors: BFT systems can withstand malicious nodes attempting to disrupt the network through actions like providing incorrect data.
Strong consistency and finality: Agreement through BFT provides strong transaction finality and consistency guarantees even under failures.
High fault tolerance: BFT protocols are designed to guarantee consensus safety as long as faulty nodes remain under a threshold.
Disadvantages:
Complex implementations: Practical implementations of BFT can be intricate, requiring careful design and testing.
Scalability limitations: Reaching consensus through mechanisms like voting rounds limits transaction throughput, though optimizations can help.
Centralization risks: BFT systems often rely on a known set of validators, introducing possible centralization based on validator selection.
Practical BFT (pBFT)
pBFT is an earlier approach to implementing Byzantine fault tolerance in a simplified manner compared to classical BFT theory. pBFT is used by Zilliqa and Hyperledger Fabric.
Practical BFT uses a three-phase commit protocol across multiple rounds to reach a consensus among a fixed set of known validators. Each round has a proposer, and validators vote to ratify proposed blocks.
Advantages:
Enables consensus with Byzantine nodes: Tolerates up to 1/3 of validators being faulty.
Strong consistency: Transactions have finality once committed.
Conceptually simple: Practical BFT is relatively easy to understand.
Disadvantages:
Limited scalability: Throughput is low due to multiple rounds of voting.
Centralized validator set: Requires known, identified validators.
Asynchronous BFT (aBFT)
Asynchronous BFT protocols use techniques like threshold encryption and erasure coding to reach a consensus without precise timing assumptions. Fantom uses aBFT in its Lachesis algorithm.
This mechanism enables consensus without synchronous network assumptions, making it robust to unpredictable network conditions.
Advantages:
Censorship resistance: All valid transactions are guaranteed to be included.
Asynchronous consensus: Fault tolerance without timing assumptions.
Cryptographic security: Uses well-studied cryptographic tools.
Disadvantages:
Complex cryptography: Threshold encryption and erasure coding add complexity.
Limited scalability: Consensus group sizes are constrained by cryptography.

HotStuff
This consensus mechanism builds on ideas in pBFT but with modifications like pipelining of consensus rounds to improve performance. It leverages a Verifiable Random Function for leader election.
HotStuff has optimizations for faster BFT consensus while preserving safety and liveness. It is used in SafeStake and Facebook’s LibraBFT.
Advantages:
High throughput: Pipelining increases transactions per second.
Cryptographic sortition: Random leader election prevents manipulation.
Strong consistency: Transactions have irreversible finality.
Disadvantages:
Fixed validator set: Requires known, identified validators.
Leader availability: Depends on the leader being available to make progress.
Avalanche Consensus
Used in Avalanche Network, in this consensus mechanism, nodes randomly query other nodes and update their preference until a consensus emerges. As preferences converge, one option becomes the dominant choice.
Avalanche introduces a novel metastable consensus mechanism based on repeated random samplings.
Advantages:
High throughput and scalability: Avalanche can finalize thousands of transactions per second and scale with network size.
Low latency: Consensus is reached quickly after a single round of queries.
Flexible incentives: Incentives for participation can be tailored based on the use case.
Disadvantages:
Strong coordination required: Proper system parameters must be chosen to ensure the network converges correctly.
Complex cryptography: Avalanche relies on advanced cryptographic techniques that can be challenging to implement.
Maximal Extractable Value (MEV) Auctions
Not a consensus mechanism per se, MEV auctions allow miners to auction block space to users who bid for priority transaction inclusion. Auctions aim to provide fairer miner compensation and transparency and is used in several blockchain including Ethereum 2.0.
It introduces an economic mechanism for block space allocation to mitigate issues with miner extractable value.
Advantages:
Sustainable miner rewards: Provides additional revenue sources for miners besides block rewards/fees.
Discourages unfair practices: On-chain auctions disincentivize extractable value extraction by miners.
User priority: Users can prioritize transactions by bidding in auctions.
Disadvantages:
Potential for manipulation: Large miners may collude or unfairly dominate auctions.
Implementation challenges: Effective auction mechanisms are complex to design securely.
User experience: Auctions could negatively impact user experience if not designed appropriately.
Radix Engine's Cerberus
This is a sharded byzantine fault-tolerant consensus protocol that achieves scalability through parallel transaction processing across shards. Not to be confused with Decentr’s Cerberus, the consensus mechanism powers the Radix Protocol.
Cerberus’ unique sharded architecture helps achieve high transaction throughput for public blockchains.
Advantages:
High scalability: Parallel sharding enables very high transaction throughput.
Security: Maintains Byzantine fault tolerance across shards.
Decentralization: Permissionless network with open participation.
Disadvantages:
Shard coordination complexity: Cross-shard communication and coordination is challenging.
Early stage: Cerberus is relatively new and lacks battle testing.
QBFT
In this consensus mechanism, validators participate in multiple rounds of voting managed by quorum slices to approve blocks. QBFT combines PoS with voting-based consensus, thereby merging the energy efficiency of PoS and BFT and achieving enterprise-grade efficiency. It is used in Consensys GoQuorum.
Advantages:
Scalability: PoS enables faster block production than PoW.
Byzantine fault tolerance: Quorum-based voting provides BFT guarantees.
Finality: Committed blocks are irreversible like in BFT protocols.
Disadvantages:
Quorum maintenance: Keeping voting quorums open and decentralized is difficult.
Complex implementations: Combining PoS and voting mechanisms introduces novel intricacies.
Federated Byzantine Agreement (FBA)
A federated Byzantine agreement system is where nodes form small groups called federations that trust each other. Each federation picks one representative node that participates in the overall consensus protocol. If a majority of these representatives, weighted by federation size, agrees on the state of the network, then consensus is reached. For instance, Stellar’s nodes choose quorum slices to drive consensus through voting rounds.
It is a uniquely decentralized approach to flexible quorum formation for consensus.
Advantages:
Flexible trust: Nodes can choose who to trust through quorum slices.
Fast finality: Reaches irreversible consensus quickly through voting.
Resilience: High tolerance for Byzantine nodes.
Disadvantages:
Complex protocol: Federated voting model is challenging to fully comprehend.
Quorum risks: Fragmented quorums may arise, inhibiting consensus.
Directed Acyclic Graph (DAG)
DAG is unique in the sense that it isn’t exactly a “blockchain” consensus mechanism. It’s a data modeling tool comprising of acyclic graphs comprising of vertices and edges, wherein the edges trace the directed path between vertices without ever leading back to a vertex to form a loop (hence, acyclic). Some example include IOTA’s Tangle, Nano, and Obyte.
It is an innovative structure that achieves consensus without dedicated validators/miners, enabling feeless and low-latency transactions.
Advantages:
Scalability: Transactions process in parallel, increasing throughput.
No fees: Users validate transactions by verifying others, removing fees from the scenario.
Fast transactions: Confirmations occur rapidly via probabilistic consensus.
Disadvantages:
Early attack risks: Vulnerable to some attack vectors in early implementations.
Complex coordination: Achieving consensus without central coordination can be challenging.
Proof of Space-Time (PoST)
In Proof of Space-Time, miners commit storage and time to gain eligibility for block creation. It discourages allocating storage only for the consensus process. The consensus mechanism is an evolution of Proof of Space introducing a time dimension to strengthen security. It is used in blockchains like Filecoin
Advantages:
Discourages attack vectors: Mitigates some PoSpace attacks by requiring storage commitment over time.
Energy efficiency: Requires minimal computation, reducing energy consumption.
Storage synergy: Can enable use cases like decentralized storage.
Disadvantages:
Implementation challenges: Adding time complexity on top of PoSpace introduces subtleties.
Hardware requirements: Requiring continuous storage over time can limit participation.
Also Read: Impending Doom or Is Web 3 the Future of the Internet
Proof of Importance (PoI)
PoI, used in NEM's blockchain, considers factors like transaction volume, account balance, and network activity to determine a node's importance. It introduces an alternative to traditional PoS mechanisms for determining validators.
Advantages:
Fair reward distribution: Rewards users proportional to their network contributions.
Encourages participation: The importance score incentivizes activity that supports the network.
Accountability: Discourages inactive token hoarding.
Disadvantages:
Complex score calculation: Designing an effective importance formula is challenging.
Centralization risks: Wealthier users may accumulate higher importance.
Proof of Activity (PoA)
Proof of Activity uses PoW mining to create and order new blocks, similar to Bitcoin. However, PoS stakeholders then vote to confirm or reject these newly mined blocks. If blocks get majority approval, they are added to the chain - otherwise, they are rejected. It is used in blockchains like Decred and Espers.
The consensus algorithm attempts to leverage the strengths of both PoW security and PoS efficiency.
Advantages:
Energy efficiency: Reduces energy usage compared to pure PoW.
Enhanced security: PoW provides robust security at the outset.
Lower barrier to entry: Transition to PoS enables broader participation in validation.
Disadvantages:
Implementation complexity: Coordinating the PoW to PoS transition adds complexity.
Centralization risks: Former miners may gain disproportionate influence as validators.
Proof of Vote (PoV)
PoV leverages direct voting by stakeholders to drive block production. It is a consensus mechanism where stakeholders vote to elect the next block producer based on their proportional stake.
Advantages:
Aligns incentives: Encourages users to vote for honest block producers.
Democratic governance: Gives stakeholders direct influence on block production.
Sybil resistance: Voting power is tied to stake holdings.
Disadvantages:
Voter apathy: Maintaining active voting participation is challenging.
Plutocracy tendencies: Wealthier users have greater influence over the voting process.
Choosing the Right Consensus Mechanism
At Global Blockchain Solution, we feel the consensus protocol is the beating heart of any blockchain network. It enables the decentralized ledger to function securely and scale efficiently.
So, the choice of consensus mechanism is crucial - it must align with the blockchain's specific goals and use case. Here, there is no one-size-fits-all solution.
For instance, public chains like Ethereum prioritize censorship resistance, so proof-of-work made sense initially. But the energy costs led it to shift to proof-of-stake. Private enterprise blockchains prefer fast finality, so they opt for BFT algorithms like Tendermint.
The pros and cons of each protocol must be weighed carefully. Even solid models like PoW and PoS have vulnerabilities. For example, PoW's mining consolidation risks could enable censorship by a mining cartel. PoS validators with a majority stake could theoretically finalize invalid blocks.
This is why most protocols require a supermajority threshold of nodes to agree before finalizing blocks. No consensus algorithm is perfect - but combining cryptographic proofs, economic incentives, and game theory minimizes security risks.
Real-world conditions matter too. For instance, Bitcoin's distribution makes censorship highly unlikely today. And Ethereum's Casper PoS uses mechanisms like slashing to discourage attacks.
If you’re uncertain about which path to tread, feel free to contact us and pick the brain of our experts.
So, there are ways to safeguard specific protocols against potential attack vectors. The bottom line is carefully assessing if a given consensus mechanism can satisfy the functional needs of your blockchain while keeping assets secure.
With the right implementation tailored to use case requirements, even protocols like PoA or DAG can serve the purpose well.
The key is ensuring incentive alignment between the consensus rules and goals of your network. This will empower your blockchain to operate as intended.
Frequently Asked Questions
1. What is an example of a consensus mechanism
As mentioned above, some examples of consensus mechanisms used in blockchain networks include:
Proof of Work (PoW): Used in Bitcoin, Ethereum, and other early blockchains. Miners compete to solve cryptographic puzzles and create new blocks.
Proof of Stake (PoS): Used in Ethereum 2.0, Cardano, and others. Validators stake cryptocurrency to earn the right to create new blocks.
Delegated Proof of Stake (DPoS): Used in EOS, Lisk, and others. Token holders vote for delegates who take turns validating transactions and blocks.
Practical Byzantine Fault Tolerance (pBFT): Used in Hyperledger Fabric and other enterprise blockchains. Validators vote to reach a consensus on new blocks.
Directed Acyclic Graph (DAG): Used in IOTA, Nano, and others. Users validate each other's transactions probabilistically by referencing previous transactions.
Proof of Authority (PoA): Used in private/consortium networks. Approved validators take turns creating blocks based on their identities.
2. What is the consensus principle in blockchain?
The consensus principle in blockchain refers to the way nodes in a decentralized network can agree on the state of the blockchain ledger and validate new transactions, without relying on a central authority.
Some key aspects of consensus principles in blockchain include:
Nodes follow a pre-defined protocol that specifies rules for consensus.
Special nodes called validators bundle transactions into blocks and verify their validity.
Validators apply cryptographic checks and protocol rules to reach an agreement.
Consensus is achieved once enough validators confirm a block is valid.
Finalized blocks are broadcast to all nodes who append it to their blockchain copy.
Consensus enables key properties like decentralization, security, transparency, and immutability in blockchains.
Different consensus mechanisms like PoW, PoS, DPoS, PBFT, etc. use varying approaches to facilitate node agreement in a trustless way.
But they all follow the core principle of nodes coordinating to verify transactions and agree on the blockchain state, without needing a central authority.
3. What is the best consensus mechanism?
There is no single "best" consensus mechanism for all blockchains. Different consensus models have trade-offs and are suited for different use cases. Some factors to consider when evaluating consensus algorithms:
Security: Resistance to attacks and ability to reach definitive consensus. PoW and BFT offer strong security.
Scalability: Throughput and ability to increase transaction capacity. PoS, DPoS, and DAG offer better scalability.
Decentralization: Broad participation of nodes in securing the network. PoW and some PoS variants enable decentralization.
Speed:How quickly transactions can be validated and finalized. BFT algorithms offer fast finality.
Energy efficiency:Electricity and computing power are required for consensus. PoS is more efficient than PoW.
Complexity: Code complexity to implement the algorithm securely. Simple protocols are better.
So the "best" depends on the specific goals and tradeoffs acceptable for a blockchain project. For a public chain, PoW or PoS often make sense, while private blockchains prefer BFT protocols.
4. Is smart contract a consensus mechanism?
No, smart contracts are not a consensus mechanism.
Smart contracts are self-executing code that runs on top of a blockchain. They encode business logic and allow automating multi-party workflows through the blockchain.
In contrast, consensus mechanisms like PoW, PoS, PBFT, etc. are focused on how nodes in the blockchain network can agree on the state of the ledger and validate transactions.
Smart contracts rely on the underlying consensus protocol to function properly. When transactions invoke a smart contract, the execution and state changes must be validated by the consensus algorithm.
So smart contracts rely on consensus mechanisms, but themselves are not protocols for achieving consensus on blockchain validity and shared state. Smart contracts extend the utility of blockchains through programmable logic - but the core consensus enables the decentralized ledger that powers them.






Comments
Share Your Feedback
Your email address will not be published. Required fields are marked *